-
Specialists caution thatAI-generated phishing messages appear refined and can evade standard email filters
-
Polymorphic attacks continuously change to avoid being detected in real time.
-
Email compromise attacks now imitate executives with nearly flawless formatting.
We’ve mentioned this previously, and we’ll continue to repeat it.
AI is transforming the landscape of cybercrime.
, and phishing is an area where it’s having the most significant impact.
Fresh insights from cybersecurity company Cofense have alerted us that AI-driven phishing attacks are now both more common and significantly more persuasive than they’ve been in the past.
These email scams are now sleeker, more refined, and designed to deceive even the most wary recipients. With generative AI tools readily available to almost everyone, malicious parties are expanding their activities at a pace that numerous companies struggle to match.
Highly evasive delivery system
In their most recent threat intelligence publication,
The Emergence of AI – Entering a New Phase of Phishing Hazards
Cofense explains how phishing strategies are advancing extremely quickly.
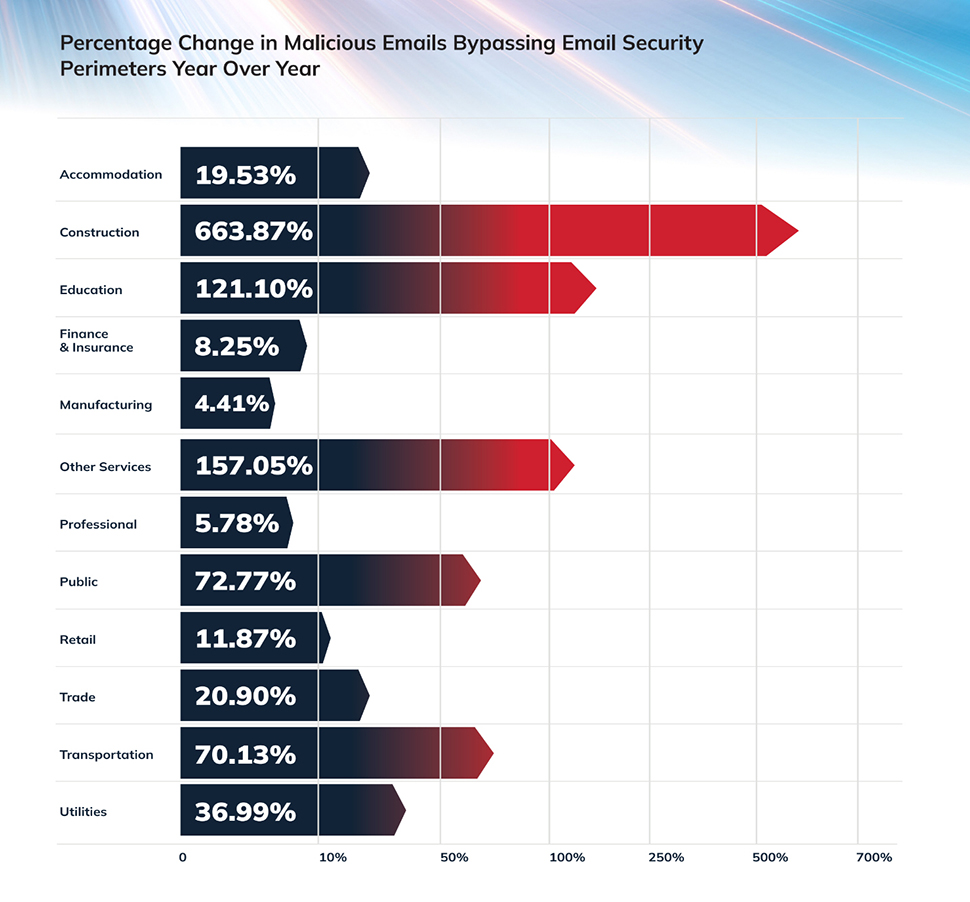
In 2024, the Cofense Phishing Defense Center identified one malevolent email every 42 seconds, with numerous such emails bypassing traditional boundary protections.
Scams conducted via email surged by 70% compared to the previous year, driven by AI’s capability to replicate tones, fake internal communications, and tailor messages with remarkable precision.
The messages currently boast impeccable grammar, precise formatting, and authentic-looking sender addresses. Frequently, they mimic high-ranking officials like C-suite executives, respond within ongoing email chains, and utilize deceptive domain names similar to “@consultant.com.”
This move towards business email compromise (BEC) has turned into a significant menace. Content created using AI no longer exhibits the usual indicators that used to expose phishing attempts, like typographical errors, misspellings, and clumsy phrasing—clues which typically pointed to English possibly not being the sender’s native tongue.
Cofense highlights polymorphic phishing campaigns as a significant issue. These evolving assaults alter their content in real-time to bypass signature-based security measures. Elements such as subject lines, sender information, and text adjust dynamically, making them extremely difficult to detect using conventional filters.
Cofense reports that malware included in these emails has become more advanced, with over 40% of the samples analyzed in 2024 representing previously unseen threats, including numerous Remote Access Trojans (RATs).
How to stay safe

Scrutinize email content carefully:
Doubt email messages related to monetary transactions, pressing demands, or unusual wording, even when they appear well-formatted.
Verify internal requests:
Should an email purporting to come from a colleague or higher-up seem suspicious, verify through established communication channels prior to proceeding.
Don’t rely on appearance:
AI-created emails frequently appear impeccable, hence concentrate on aspects like context, timing, and substance instead of merely focusing on its appearance of professionalism.
Steer clear of clicking on unverified links:
Move your cursor over hyperlinks to see where they lead before clicking them, and refrain from downloading attachments from unknown or unsolicited communications.
Utilize security measures that extend past the boundary:
Seek out options that provide post-delivery analytics and threat responses driven by behavioral patterns rather than solely relying on signatures.
You might also like
-
Stay protected with the
best antivirus tools
around -
We’ve also gathered together the
best free antivirus
solutions -
Japanese companies are receiving millions of phishing emails.
Enjoying this piece? To read more articles like this one, follow us on MSN by tapping the +Follow button at the top of the page.
